

Smart and vulnerable go hand in hand in the world of cyber security. In the rush to connect everything, it is not only Information Technology (IT) systems and devices that are subject to vulnerabilities, but also Operational Technology (OT) which is used to control industrial equipment that interactswith physical environments.
The proliferation of malicious activity, with cyber-attacks becoming more aggressive and widespread, was already highlighted in the World Economic Forum’s Global Risks Report 2022.
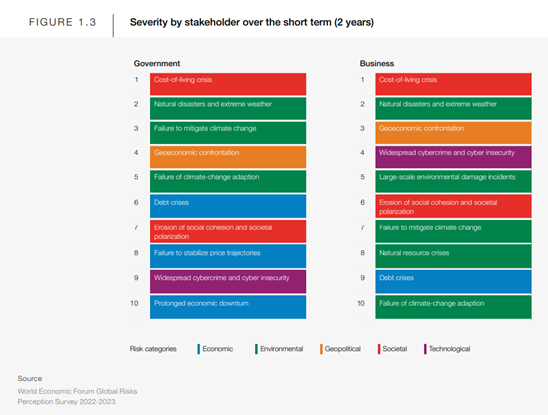
“Widespread cybercrime and cyber insecurity” now ranks in the top 10 of the most severe risks over the next decade, as per WEF’s 2023 Report. Respondents see this as a persistent threat and a strong driver of other risks. Business respondents even rank it as the 4th most severe global risk over the next 2 years.
In this scenario, the convergence of OT with IT is resulting in an escalation of cybersecurity threats. Hacktivists are increasingly targeting OT systems, which will increase OT-related attacks around the world. Industrial systems and operations are open to the same kinds of security threats as IT systems, making the security of OT assets indispensable.
New risks and challenges from OT-IT convergence
OT systems control essential processes and operations in industries such as manufacturing, energy, transportation, and healthcare. These systems are increasingly connected to the internet, making them vulnerable to cyber-attacks.
An effective OT security strategy can help prevent these attacks and mitigate their impact if they occur. It helps protect critical infrastructure and assets from cyber threats, including physical damage, data breaches, and operational disruptions.
An OT security strategy should include several components, such as:
Asset visibility
Having a comprehensive inventory of all OT assets, including devices, software, and systems. This can help IT and OT teams identify vulnerabilities and prioritise security patches and updates.
Segregation
Segregating OT networks from other networks, such as corporate IT networks, can help prevent unauthorized access to OT systems and reduce the risk of malware propagation. At the same time, today's business demands are driving OT-IT convergence. Hence secure OT-IT integration is one of the key focus areas for security development.
Protecting intellectual property
Protecting intellectual property and sensitive information stored in OT systems is critical to prevent data breaches and maintain the confidentiality of trade secrets.
Situational awareness
IT and OT teams should have real-time situational awareness of OT systems, including network traffic, system logs, and security alerts, to detect and respond to security incidents quickly.
Continuous monitoring and testing
Regularly monitoring and testing OT systems for vulnerabilities and weaknesses can help identify potential security gaps and ensure that security controls are effective.
Visibility of OT environment with asset management
As part of its customer OT security strategy, Wärtsilä has selected Tenable OT Security™ to manage its OT asset inventory collection and provide holistic visibility into its OT environment. With Tenable OT Security, an industrial security solution for the modern industrial enterprise, Wärtsilä can identify assets, communicate risk and prioritise action all while enabling its IT and OT teams to work better together.
The deployment allows Wärtsilä to answer customers’ questions around asset delivery, reduce supply chain risks and take a proactive stance on cybersecurity. Wärtsilä will extend the Tenable solution to its customers, allowing them to visualise their own OT environments.
This includes information about current project delivery whilst also detailing cyber risks within a customer’s environment that need to be addressed. It allows both parties to move beyond reactive cybersecurity to a proactive exposure management program.
“With Tenable OT Security, we can help our customers to visualise their own OT environment. This allows them to adhere to the evolving compliance landscape and ultimately assists in protecting critical infrastructure.”
You can read more in the press release and the detailed use case on Tenable’s website
Challenging an OT environment with hacking skills
To stay updated with the latest cybersecurity trends and demonstrate the capability to face the challenges that the future will bring to OT, Wärtsilä recently participated at Disobey Nordic Security Event 2023 and put OT hacking skills to the test.
Wärtsilä brought a fully automated and remote-controlled factory environment, while partnering cyber experts from Elisa Santa Monica teamed up to protect it in the “OT Village” area.
Participants were challenged to hack their way through the systems, with more than 34 teams competing over two days and 6 of them completing the challenge.
By attacking a real automation environment, Disobey participants could understand that a successful cyber-attack to an Industrial Control System has real-world consequences – from human safety to business continuity.
With the proliferation of malicious activity, a robust OT security strategy is definitely a very good idea. More than that, it is imperative to leverage the smart side of connectivity while effectively managing vulnerabilities in industrial environments.
Did you like this? Subscribe to Insights updates!
Once every six weeks, you will get the top picks – the latest and the greatest pieces – from this Insights channel by email.
